In the recent past we have had lots of hacking cases internationally. It seems like there is a hacking trend that is on the rise and more and more computer systems are being easily brought down by hackers who seem to relish in the joy of making organizations, institutions and even government agencies vulnerable to further attacks. Ethical hackers are being tasked with the hard work of ensuring that any perceived threats in organizations are identified and sealed before the black hats can get their hands on such a loophole.
When one is trying to capture a monkey, one of the methods employed is the use of a honey pot. The honey is put in a pot that has a small opening that can easily fit an open hand. So when the monkey dips in its hand and picks the honey, they cannot get their hand out because now its hand is balled up in a fist. This traps the monkey there and one is able to capture the animal. One of the methods that the white hats are employing against the hackers is the use of Honey pots.
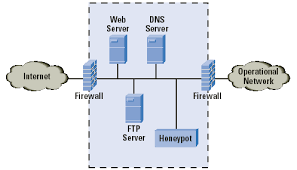
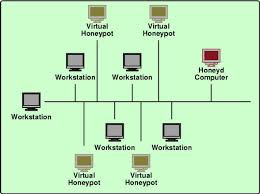
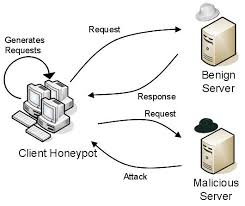
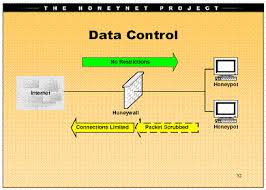
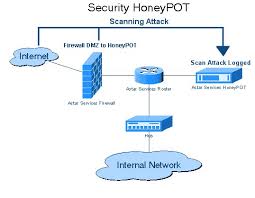
A Honey pot is a system that is deliberately installed to attract and trap people who are out to penetrate other people’s computer systems. The system is a decoy of the original system but greatly mirrors the original system so that the hacker will see the need to penetrate it not only once but many other times too. The honey pot is not meant to replace other conventional security methods but is meant to work in tandem with them as an additional piece of security. The honey pot system is also used for information gathering and as a deception tool for intruders. It undergoes minor system modifications to enable it to record the activities of the intruder and thus help in eventually tracing them. The insinuation here is that once an intruder breaks in, there will be other subsequent visits to the site.
There are two main reasons as to why honey pots are set up. The first one is to learn how intruders probe and attempt to gain access to your systems. The minor system modifications done on a honey pot allow it to record the intruders’ movements. These past records are able to shed some light into the mind of the intruder and thus reveal his attack methods. This in turn enables the organizations to protect their real site from any future attacks. The other reason is to gain information that can lead to the capture and prosecution of the intruder. This refers to information that an organization can easily forward to the law agencies and that will be enough to get the intruder some jail time.
Honey pots seem to be very effective but just like everything in life it has its limitation. One of its limitations is that the information achieved through the honey pot is actually not obtained in a very legal way because it’s deceptive. This means that in the case of prosecuting an intruder the evidence from the honey pot may be ruled off as inadmissible before a court of law. This will even be more difficult if the case is brought up against a non-technical jury who might not easily understand its legitimacy as a piece of evidence.
Putting up counter measures against hackers is a practice that every organization should heavily invest in to ensure that their businesses are well protected and face no risks from any malicious intruders. At Kenvision Techniks, we understand the need to operate in a secure and reliable system and thus we offer an Ethical Hacking & Countermeasures Training Course that will meet your security needs and keep you on top of your business, worry-free!